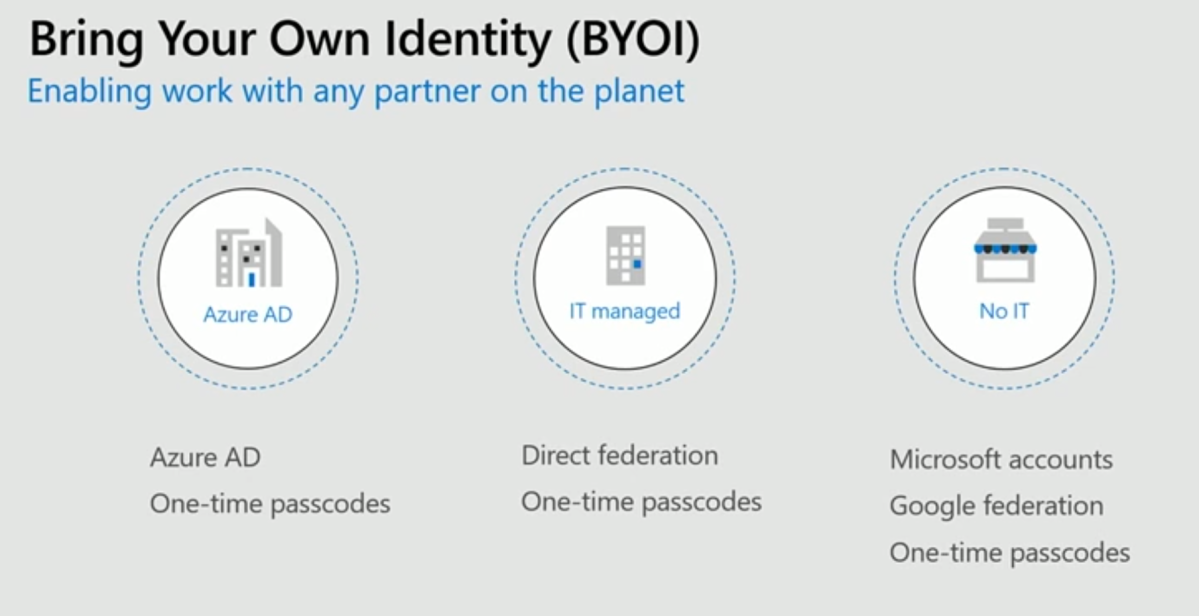
Requested multiple times Microsoft has now released the usage of Javascript in Azure AD B2C custom policies.
Public preview: JavaScript and page contracts in Azure Active Directory B2C policies
This currently only works with custom policies from the Identity Experience Framework.
You need to select a different DataUri in your ContentDefinition by selecting an immutable package that won’t change during it’s lifetime.
See: https://docs.microsoft.com/en-us/azure/active-directory-b2c/page-contract
After that you can add Javascript to your content, see the following page for details and some samples:
https://docs.microsoft.com/en-us/azure/active-directory-b2c/javascript-samples